These are only suggestions, the way it is really going to look like is pretty much software vendor (SV) dependent.
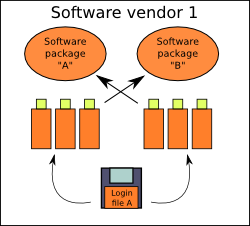
Simplest form. A single login written at all devices SV is the owner of.
Every developed software package (SP) can access all the devices, though
each solution can have different licensing algorithms, requiring a different
license to be written at the device.
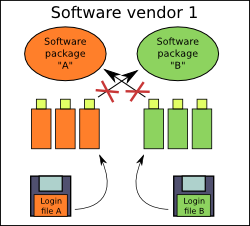
Software solution based device access. Every software solution is using
own Login to unlock the device (PK). In presented case, SP B
is not capable to unlock the devices dedicated for SP A,
therefor devices can not be swapped between SP-s.
It improves security a lot.
The same as in 1st case, binary form of licenses might be identical or completely different.
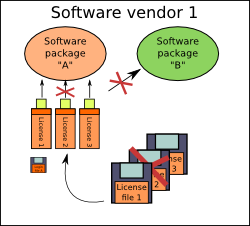
Comparison of binary data between device and software memories
might be enough for the start. For production environment, it
is worth of implementing some more advanced algorithms.
It will benefit a possibility of using different credentials for each client.
Making one license (and device using it) invalid will not block remaining devices out there, used by others.
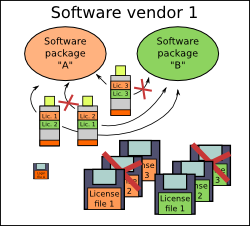
Advanced and very effective case. All SP-s use the same login to unlock
devices, but the licensing data is kept in different memory segments of the
device. This way a single device can be used to license few products.